Federal Rules Expand the Scope of Your Customer's Data Protection
In case you were wondering about the onslaught of regulator or investor requests for cybersecurity plans, risk assessments, and MFA certifications, it all has to do with FTC regulations passed last year that go into effect December 9, 2022. The FTC has extended the deadline for compliance for 6 months, making the new deadline 6/9/2023.
eCFR :: 16 CFR Part 314 -- Standards for Safeguarding Customer Information
In a nutshell, our customers have all of the tools to meet these requirements in the 2-90 IT Security Plan. These include:
- Employee Training
- Risk Assessment
- Third-Party Vendor Reviews
- Data Breach Response and Remediation
Small companies - responsible individual
For small firms, you should assign a responsible individual who is knowledgeable about the technology aspects of your firm. They do not need to have a degree in cybersecurity. However, they should know all the firm's tech and communications infrastructure and have the capability to completely answer the cybersecurity questionnaire. If the individual is NOT able to answer the questionnaire, you MAY designate a third party, such as an IT consultant. We caution small companies against signing big contracts if the firm's technology consists mostly of leased cloud computing assets, such as LOS, document storage, and email. Even third-party apps, like online 1003s, should come with some tech support, and you can designate a 3rd party (even the vendor) specifically for those types of risks.
Don't "Build Castles" - Use the Tools you Have
We really try to avoid creating additional work in the form of a separate workflow for compliance-related matters. That's why you should use some of the resources you already have to meet some or all of the requirements.
- Credit Bureau Audits - If you have the ability to pull credit reports yourself (instead of just through your investor/wholesaler directly) you likely have a credit bureau service provider. This firm is responsible for evaluating your firm (usually annually) and providing a risk assessment based on that evaluation. That should be a foundation. Review their report against the overall questionnaire to see how many items are covered.
- By the way, bureaus are conducting these audits furiously as a part of the new rule's implementation
- State Certifications - keep a copy of any questionnaire you complete to assess your technology. THIS COUNTS AS AN AUDIT or RISK ASSESSMENT
- When you sign up with a tech provider, get their SOC or ISO certification information. Use the vendor's reviews as your own.
- When getting training, make sure you keep a copy
- Read your policies and procedures - if they don't make sense, get a plain English translation!
Speaking of Plain English - here's our summary of the IT/Cyber Security Plan requirements that you can use as a checklist.
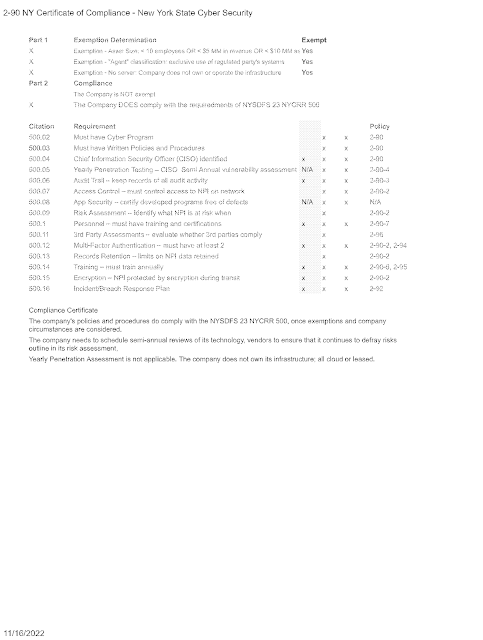
New York Cybersecurity Certification
The Section NYSDFS 500 updates that went around earlier this year include the updates from the FTC's rule. The changes do not represent a departure from current best practices but memorialize the requirements in the FTC's Safeguarding rule.
Remember that the certification only captures information on what you are doing. Policies and procedures should reflect this information; they don't replace your implementation.
You can request help completing your Cybersecurity Certification here


No comments:
Post a Comment