If you own your network infrastructure, big changes coming to New York
For MortgageManuals.com customers, your Information Security Plan covers the requirements
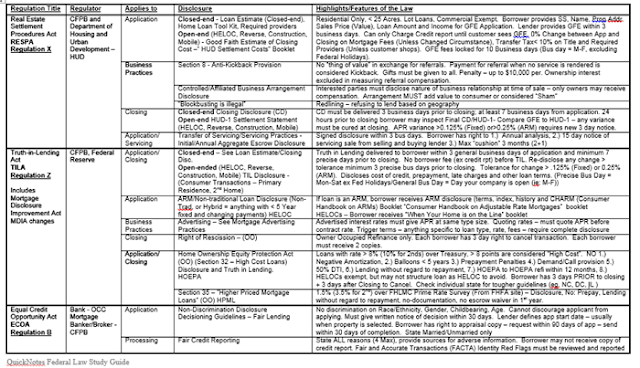
New York State licensed financial entities have received notice of new specific requirements for cyber-security. Rules went into effective March 1, 2017, and compliance deadlines start August 28, 2017. Cyber-security is a synonym for information security when data is stored or accessed via an electronic information storage and retrieval network. In other words, cyber-security deals with network security in addition to basic information security.
Complete text of Cyber-security Rule
At the heart of the requirements, aside from standard information security remediation, companies must have some form of dual factor authorization. If you use a token or mobile password in addition to your password, you probably already comply.
Are you Exempt?
The law contains a number of key exemptions:
Exemption - Asset Size: < 10 employees OR < $5 MM in revenue OR < $10 MM assets
Exempt from 500.04, 500.05, 500.06, 500.08, 500.10, 500.12, 500.14, 500.15, and 500.16
You must still have policies and procedures, you must control access, conduct a risk assessment, identify if 3rd parties have an CISP,
Exemption - "Agent" classification: If you use someone else's system (such as wholesaler's or investor's)
Exemption - No server: If you don't own and operate the infrastructure
Exempt from 500.02, 500.03, 500.04, 500.05, 500.06, 500.07, 500.08, 500.10, 500.12, 500.14, 500.15, and 500.16
You must still control access, conduct a risk assessment and identify if 3rd parties have a CISP.
IF YOU ARE EXEMPT, YOU MUST FILE AN EXEMPTION BY AUGUST 28, 2017. A copy of the exemption certification is on the last page of the announcement - click here.
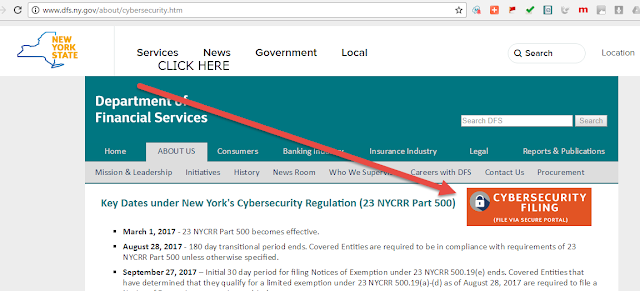 |
| To file your exemption certificate go to http://www.dfs.ny.gov/about/cybersecurity.htm and click on the large orange filing button graphic. |
If you are NOT Exempt
For entities which are NOT exempt, we identify where your policies and procedures meet the requirements. While there are a number of preparations entities must make to comply, unless you maintain your own servers the actual, physical changes normally will be undertaken by your third party infrastructure provider.
If you obtained your information security policy from us, you may share it with your infrastructure vendors, as it addresses the requirements:
Section 500.02 Cybersecurity Program
By virtue of having a written policy in place, you comply with this section. In addition, our policy states the protocol for testing the program, another requirement of this section.
Section 500.03 Policy
This section defines what must be in your policy and procedure. We identify those things that are the responsibility of the network provider, and those which are the responsibility of the mortgage company.
(a) information security; the actual plan for protecting NPI - #1 - mortgage company
(b) data governance and classification; the system by which you identify data that is NPI - #2 - mortgage company
(c) asset inventory and device management; infrastructure provider
(d) access controls and identity management; infrastructure provider & #3 password policy mortgage company
(e) business continuity and disaster recovery planning and resources; #4 mortgage company
(f) systems operations and availability concerns; infrastructure provider
(g) systems and network security; infrastructure provider
(h) systems and network monitoring; infrastructure provider
(i) systems and application development and quality assurance; infrastructure provider
(j) physical security and environmental controls; #5 mortgage company
(k) customer data privacy; #6 mortgage company
(l) vendor and Third Party Service Provider management; #7 mortgage company
(m) risk assessment; #8 mortgage company
(n) incident response. #9 mortgage company
Citation
|
Requirement
|
Addressed in Info Security Plan
|
500.04
|
Chief Information Security Officer (CISO) – you must install one, if you don’t have one
|
2-90 #5
|
500.05
|
Penetration Testing – CISO must conduct yearly, vulnerability assessment every 6 mos
|
2-90-4 #7
|
500.06
|
Audit Trail – keep records of all activity
|
2-90-3
|
500.07
|
Access Control – must control access to NPI on network
|
2-90-2 #3
|
500.08
|
App Security – certify developed programs free of defects
|
N/A
|
500.09
|
Risk Assessment – Identify what NPI is at risk when
|
2-90-2 #8
|
500.10
|
Personnel – must have training and certifications
|
2-90-7 #9
|
500.11
|
3rd Party Assessments – evaluate whether 3rd parties comply
|
2-90-4 #7
|
500.12
|
Multi-Factor Authentication – must have at least 2
|
2-90-2 #3
|
500.13
|
Records Retention – limits on NPI data retained
|
2-90-2 #10
|
500.14
|
Training – must train annually
|
2-90-6 #9
|
500.15
|
Encryption – NPI protected by encryption during transit
|
2-90-2 #11
|
500.16
|
Incident Response Plan
|
2-90-2 #2
|
 |
| Page 1 - Information Security Plan - Showing References to Requirements |
 |
| Page 2 - Information Security Plan |
 |
| Page 1 - Disaster Recovery Plan/Business Continuity Plan |
 |
| Page 1 - Customer Privacy Policy |